Security assurance of cloud systems: A data-driven perspective
Cloud systems are intertwined in many modern human activities and, more importantly, they play a crucial role in business critical domains. Continuity of service, downtime reduction, and performance of cloud systems are widely recognized concerns by practitioners. At the same time, data breach episodes, which caused credentials and credit card numbers leaks such as Linkedin (2012), Global Payments (2012) and TripAdvisor (2014), are posing new societal and economic challenges. Security attacks have become surprisingly sophisticated over the past 15 years. Emergent threats leverage the widespread network connectivity to conduct complex and highly coordinated attacks involving several distributed nodes.
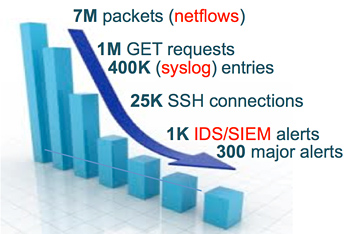
Analysis of monitoring data collected under real workload conditions plays a key role in gaining insights into system activities and in pointing anomalies, either accidental or malicious. Cloud systems are currently equipped with a variety of independent monitoring tools, such as system and application logs, network audit, intrusion detection systems (IDS), and operating system-level monitors, as shown in Figure 1. A medium-scale data center generates several gigabytes of monitoring data per day, which represent a goldmine of information. Nevertheless, despite the availability of large data sources, the real challenge is to take competitive advantage from them.
Critiware has a long lasting experience in data-driven measurements and analysis. We serve a number of customers in real cutting-edge application domains. Our work encompasses production and quality of data monitoring, filtering, and analysis. Key contributions of our activities in the area of large-scale data centers and Clouds include the analysis of credential stealing attacks, incident and anomaly detection, and reliability studies.
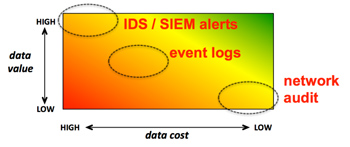
The amount of data available in a cloud system is an underexploited resource. Massive user base, increasing network traffic, and failure rates cause the generation of large volumes of data that overwhelm operations teams. While each data source can have a precise role to gain insights into a security attack, forensics is still strongly manual and time consuming. It should be noted that data available in a cloud system have different cost and value from a human perspective, as indicated by Figure 2. For example, network audit is relatively simple to be generated (low cost). However, it is extremely hard navigating across thousands numeric network records (low value). On the other end of the spectrum, while it is hard to generate IDS alerts due to the effort it takes to implement detection rules (high cost), IDS alerts can provide strong evidence of ongoing attacks (high value).
Data analysis lacks established end-to-end procedures and relies on ad-hoc techniques and tools to deal with format and semantic heterogeneity. The new generation of data scientists shall be able to infer predictive insights from available data, which enable proactive response actions. The point is not establishing if an attack occurred, but when an attack will occur. Run-time data will play a crucial role towards this objective. However, data-driven security assurance of cloud systems is still an open and challenging research field.
Please visit https://www.critiware.com/research/ for related applied research and projects on data analysis topics.
